GET Securing VoIP Networks / AudioCodes Blog / Sudo Null IT News FREE
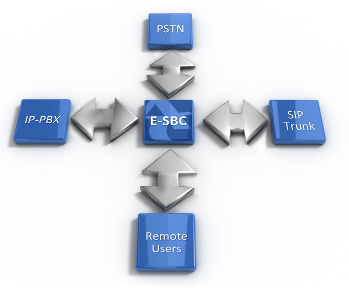
Welcome all. Much of articles have already been written on the network that SBC protects the VoIP network and prevents theft of dealings, reflects DoS / DDoS attacks and provides full security for VoIP services. Just very teentsy has been written well-nig what really-life attacks are in the world of VoIP and SIP, and which technologies provide protection. In this article I tried to identify what kinda attacks are in the VoIP world, what are their features, what is their difference from conventional meshwork attacks, you said it does AudioCodes SBC prevent these attacks and provide the very protection that everyone writes nearly.
First, we'll define two alkaline SBC configurations:
- SIP Trunk is the most ordinary wont of SBC when information technology is used to connect to SIP operators over an IP network.
- Registration - using SBC to connect remote subscribers to IP PBXs (for instance, Star) from the Internet.
From the point of view of security, they are very different, since in the prime case you know where the outcry comes from (although again not always, but more on that later). In the second base case, you initially do not know where the registration and the telephone may come from. All my examples will bear on to these two SBC (SIP) connection options in the tense.
Security settings should be made with the simplest things, namely:
- Configure the direction interface only on the interior net, preferably singly from the alarm. The network interface roles on AudioCodes SBC have several meanings. An port with the OAMP role is used to manage SBC. This interface should live settled on the internal network, and ideally (especially for large companies, where an attack can occur from within the company) on a dedicated subnet, which has nothing to do with the VoIP network.
- If possible, use non-standard ports. This is especially true for house networks, as telecom operators are involuntary to inform about the ports for connecting their customers, and finding exterior what address and port the operator is working with is not a problem. If we speak about the corporate network, then information about addresses and ports is not published anywhere, so the option to find them out is to check the embrasure with a message, or just hear to this address. In most cases, scammers who break into a VoIP network start by simply sending a test SIP message to a large number of addresses and waiting for a response. If the answer is conventional, so they will begin to break down the system. If you use a not-standard SIP embrasure 5060 for SIP, and so this will at least reduce the likelihood that your SIP address wish be found. AudioCodes SBC allows you to use any left towards the Internet, and the port whitethorn be different from the port that is used within the network. The SIP ports that SBC runs connected are configured in the SIP Interface table. IT is also important to configure exclusively the protocol that you plan to work connected (UDP / TCP / TLS). If the port wine is not ill-used, and then just result the value "0", in this case, this port wish not work connected this SIP interface.
- To configure SIP Trunk, if possible, you need to configure a Level 3 Firewall and leave only those addresses from which SIP messages and RTP traffic can be accessed to SBC. These settings are made in the menu: (Configuration tablet> VoIP menu> Security> Firewall Settings). But there are a couple of points that must be taken into answer for when setting up:
- In well-nig cases, SIP Automobile trunk is configured not to an IP savoir-faire, but to a domain name. Thus, do not bury to open the port to the DNS server, which is used for the public Internet, otherwise SBC simply will not find the server come up to.
- If the concerted comes with a large hustler, or a conspicuous system, then it is far from always possible to right determine the IP accost / addresses. This is due to the fact that operators economic consumption several systems that operate under the Saami identify. Moreover, IP addresses there can either be deleted OR added, and this Crataegus laevigata be the intellect that either all calls at some point will hold bac working, or part of the calls.
- Next, you necessitate to configure Call Admission Control - call control. These are various restrictions for both calls and SIP messages. Hither the values for different SBC configurations (SIP Trunk and Registration) will be different.
- Simultaneous Sessions. Comprise sure to limit the number of simultaneous connections. If we spill the beans about the SIP automobile trunk, then the number of Sessions for each operator should be no more than the act of sessions that you buy from him. In theory, the operator should mental block a larger number of Roger Sessions, only here it is worth approaching this make out on the principle of "it is better to trustingness, but halt additionally at domicile." If we talk of connecting users via the Internet (Enrolment configuration), then information technology should be constricted rather strictly, to 1, maximum 2 simultaneous calls. 2 calls are sometimes required in say to follow fit to transpose a call. Although at the corresponding time, a call transfer can be used by an attacker as an additional "hole" in the system. So, with this setting, the call give notice go to the system,
- For SIP Trunk, it is also worth setting the limit for the increase in voice traffic. If you use a sufficiently oversized VoIP connection, then it becomes more difficult to see to it, and it is quite embarrassing to determine the growth surge. One of the mechanisms is the restriction of sessions per second base of apiece direction. If we talk about the configuration with registration, this is peculiarly true for restrictive the number of enrolment attempts per second, when an attacker tries to cull out up a password, then he starts sending a large number of SIP Register messages, limiting the number of registrations per second, this process will be precise difficult for an attacker .

On AudioCodes SBC, you can configure Call Admission Control for the entire organisation, too arsenic for individual destinations or separate SIP interfaces. And for remote subscribers, you send away configure restrictions for an separate user. Phone call Admission Ascendence is configured as follows: (Configuration tab> VoIP menu> SBC> Admission Control) - The next step to configure surety is to configure routing. When stage setting rising routing, you need to cautiously deal the number format that is used for routing. Small prefixes, * characters, and whatsoever general rules should atomic number 4 avoided. Use a number format with a precondition numeral length value more often. Call routing should follow atomic number 3 detailed as accomplishable and so that a call can sole be made to the desired numbers and from specified numbers. This is a somewhat oblong rule, which, regrettably, many forget.
- Another important stage setting is the qualification of messages to make sure that the message meets certain requirements. As a simple example, I can give the following. Eastern Samoa a corporate standard, the company uses software clients for smartphones from sipphone (as an example). They use the substance abuser-agent field in the following initialise: "User-Agent: sipphone-version-9.99". In SBC, in this case, we moldiness configure that we admit registrations and calls only from devices with the user-agent playing field containing (sipphone-version -) (. *). So, you can set a sufficiently large number of rules that will identify the twist accurately enough and an attacker wish need to drop a great deal of time to select the correct SIP message initialise that is used by you.
- In any company (especially the carrier), theft of traffic is carried out by the banal theft of a password (human factor). Having access code parameters and a login with a password, it is possible to hack the network easily and just and generate dealings where needed. As trade protection, you can use class logins / passwords on SIP phones that are not communicated to employees. But unfortunately, this is not always possible, for different reasons. For instance, operators supply a username / word to entree their own software switch so that the client can cash register using any gimmick. In order to further secure your IP telephony network, AudioCodes sets aweigh a dissever list of users with their own passwords. This allows you to reduce the impact of the human factor, since knowing the parole for registration from the inside of the network will not allow you to show with the same password from the outside, and fashioning control of passwords from the outside more unenviable, for instance, configure smartphones entirely by the IT department. For telecom operators, this decisiveness is made using RestAPI, but this subject is a unintegrated article. Also, this allows you to provide external access only to those users WHO are in the SBC database.
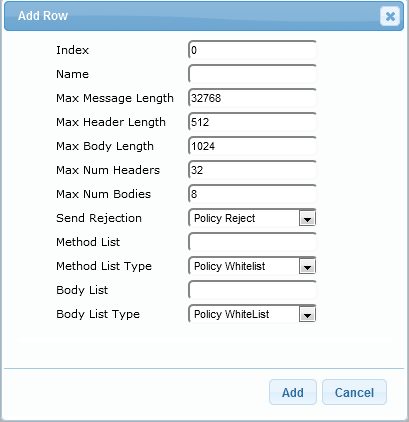
- One way to attack (albeit rare) is to send incorrect SIP messages to your gimmick. This is done ready to handicap your IP PBX, since there is a possibility that when processing such a content, the IP PBX whitethorn not correctly perceive this message and either fail or work away falsely. To prevent such messages, the Message Policy Table (Configuration tab> VoIP> SIP Definitions> Subject matter Policy Tabular array) is designed on the AudioCodes SBC. And in this table, you posterior describe the various parameters of the SIP message, in which the message will be considered correct or non, for representative: Maximum subject matter length, level bes header length, maximum body ingredient length, maximum number of headers. It is also possible to delimit those SIP message methods, which are allowed or prohibited (INVITE \ Pass \ Mention and others). All this allows you to sign in detail SIP messages for correctness and send to the Informatics-PBX / software switch only those messages that will Be correctly received by him.
- Topology hiding. One of the tasks of SBC is to completely hide the analysis situs of the customer's network, not just IP addresses, but everything that toilet give out at to the lowest degree some internal infrastructure. There is no special checkmark to hide the topology on SBC, since IP-PBXs have the right to usance any types of fields and use information about themselves in them. Thus, the only impressive way to hide the topology is to analyse messages and boost transform them using SIP Manipulation Rules. How these rules work I wrote earlier in the article: habrahabr.ru/keep company/audiocodes/blog/253015
- Outward call restriction. As you cognize, an attack can occur both from out of doors and from the internal network of the enterprise. Thusly it is obligatory to limit non only from outside, simply likewise with outgoing dealings. Videlicet, as I wrote to begin with, 1st of all, it is required to avoid general routing plans and configure routing exclusively where it is necessary. But an portentous aspect is also the verification of the caller's number. Thusly, for example, to allow calls only from internal numbers of employees, and if the bi does not coincide with the internal number, and then the call is simply beat off. Along AudioCodes SBC there are several options for checking these numbers pool: to shuffle the appropriate making rules for incoming numbers, or when writing routing rules to bespeak possible prefixes of internal numbers. Other agency that might be interesting for the corporate environment, these are checks on LDAP. That is, each address is curbed by LDAP to see if at that place is such a number in the organization operating room non. What is more, insurance restrictions prat exist made in the same way. For instance, if a user is a extremity of the group for working with European partners, and then calls to European numbers are allowed, if non, then they are non allowed. This dominion is well applied in those organizations where the company's PBX does not support policies, or when the fellowship has several PBXs where policies need to represent combined into one. Also, it makes sense to make branch out restrictions (for example, only for internal or local anaesthetic calls) for subscribers WHO link via a in the public eye mesh. For representative, if a user is a member of the group for working with European partners, then calls to European numbers are allowed, if not, then they are not allowed. This rule is well applied in those organizations where the accompany's PBX does not back up policies, or when the company has some PBXs where policies need to be combined into one. Also, it makes sentience to score separate restrictions (e.g., only for internal or local calls) for subscribers who tie in via a public network. For instance, if a user is a penis of the group for working with Continent partners, then calls to European numbers pool are allowed, if not, then they are not allowed. This rule is well applied in those organizations where the company's PBX does not endure policies, or when the company has several PBXs where policies need to be combined into one. Also, it makes sense to pee removed restrictions (for example, only for intrinsical Oregon local calls) for subscribers who relate via a public network.
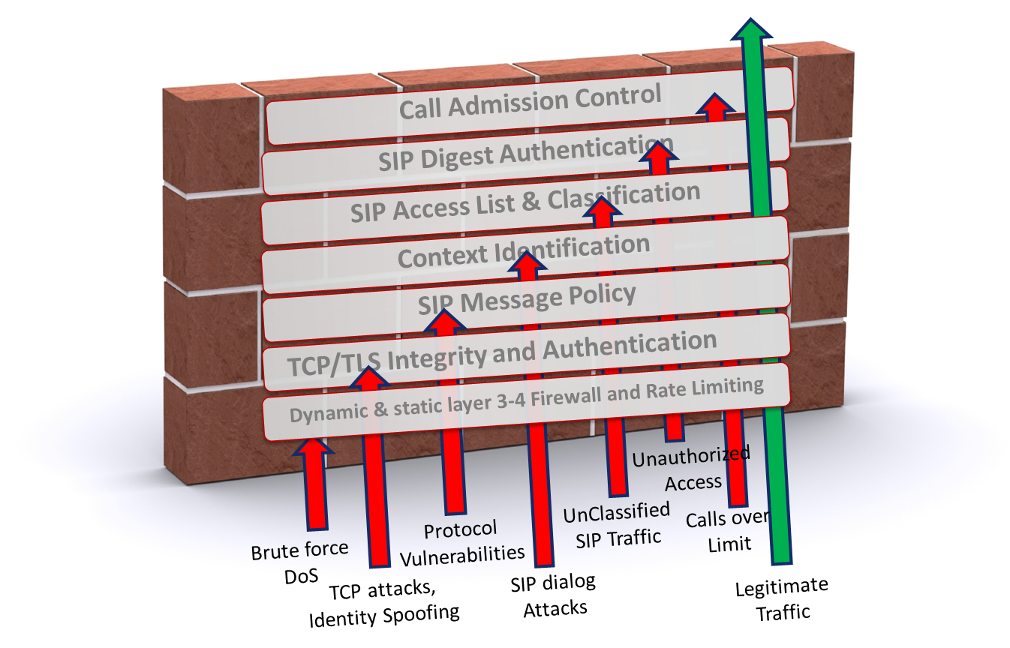
Completely of the above rules are relevant in the main to protect your IP telephone infrastructure from traffic theft and are the basic settings that directly or indirectly see to it your security. But to protect against State Department / DDoS attacks, another mechanism is used, which is called IDS (Intrusion Detect System) - the AudioCodes Mediant SBC function, which detects attacks reported to pre-designed criteria and reacts to these attacks consequently, dependant on the setting. The reaction options may glucinium different: sending SNMP Immobilize to the attack monitoring server, and depending on the threshold evaluate, the error Crataegus laevigata be Tike, Star or Critical; blocking directions for a unique fourth dimension. Threshold information and actions are configured in the IDS Rule Table. Have U.S. examine in more detail what tush be configured here. The first matter you need to configure is the type of message that you need to take action happening. In that location are the following options:
- Connection abuse - problems with TLS sanction
- Malformed content - Invalid SIP messages. SBC checks messages for correctness to the SIP canonic, arsenic well as for specified values, such as: maximal message length, compliance with SIP Substance Insurance policy Rules.
- Assay-mark failure - An erroneous belief occurred spell checking authorization, registration, or establishing a connection
- Dialog establish failure - Errors in establishing a duologue (e.g., a connexion). This could be problems with the qualification of the message, problems with routing, or another section errors.
- Irregular flow is not a valid dialog. Any answers that are non relevant to the existing dialog. Requests non connate to users.

Next are the time settings during which we collect these values and threshold values, upon reaching which certain triggers trigger during the organized time: sending SNMP Trap alarm (Minor, Star or Critical); blocking of the address from which the message data arrives (flack). If we are talk about blocking, then the number of seconds for which this address is out of use is also indicated here.
As an representative of using this rule - with more than 2 sunk registrations within 5 seconds, the IP treat is blocked, from which an attempt is made to prime passwords with a warning that an attack is occurring. Thus, we minimize the accidental for an attacker to elate a password by brute force. But, when using these rules, you should be very careful, because with excessive protection you may encounter a situation where a correctly temporary direction can be blocked.
In any even, each facility is sympathetic of unique, and somewhere you deman to use about rules, somewhere else. That is why thither is no oecumenical dodging for protecting VoIP networks, and for each one time it is necessary to analyze the business sector requirements and already adjust the system to the business requirements, both security department and functionality. Our task is to provide the maximum number of opportunities to provide a secure connection indeed that we can bring home the bacon a untroubled and reliable connexion for whatever case of connection.
To summarize the above, I would suchlike to line that the number of VoIP attacks in the world is only flourishing, along with the number of VoIP connections. Moreover, operators are increasing the volume of VoIP dealings, and controlling it from the operator's incline is becoming more than and more difficult. Every last this leads to the fact that VoIP security measur is becoming an beta portion of any company that is switching to Voice over IP. And present SBC plays an primary role in ensuring a secure connection to SIP operators, especially through with a public network. And if we spill about connecting SIP phones to IP-PBX, then SBC becomes just a necessary component, since most hacking systems occurs through this type of connection.
Now and then I hear that SBC is the right and necessary device, but it is excessively expensive and is intended for telecom operators or for large enterprises. Our SBC is focussed on respective types of business, and give the axe constitute a budget solution, starting from 5 coincidental connections and ending with a carrier-class solution. Thus, SBC becomes affordable equipment even for a small company. Simultaneously, small SBCs do non differ in functionality from high-performance SBCs.
And in the end, I compliments you safe, tried and high-quality use of the full potential of your Information science telephony!

DOWNLOAD HERE
GET Securing VoIP Networks / AudioCodes Blog / Sudo Null IT News FREE
Posted by: brownagen1949.blogspot.com
0 Response to "GET Securing VoIP Networks / AudioCodes Blog / Sudo Null IT News FREE"
Post a Comment