GET How to make a password secure and memorable / ua-hosting.company Blog / Sudo Null IT News FREE
Passwords guard our data. And the degree of their dependableness plays an important theatrical role. It is clear up that a complicated password will not be easy to crack. Here are just a lot of personal accounts and systems requiring authorization, a lot. And remembering dozens, if not hundreds of assorted combinations of characters - is almost impossible.

How to make the word more reliable and not blank out IT? There are several options…
Easy replacement cipher
Replacement ciphers - a category of encryption methods that exists almost as much as the alphabet. Its essence consists in replacing letters with separate letters, numbers racket or symbols (reference to cryptography).
Without delving into the features and subtleties of the cipher, you can buoy choose the simplest encryption method - the one where apiece letter is replaced away the next unrivalled in the alphabet. For example, take the words "cast" and "hot dog". We encrypt: after with in the alphabet goes d ( c = d ), after a will be b ( a = b ), recovered, after t follows u ( t = u ). The same formula is for the second word: d = e , o = p , g = h. Eastern Samoa a result, we get down two ciphers - dbu and eph .
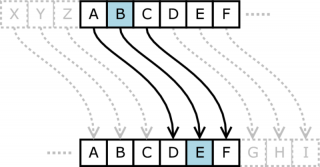
The nonentity of a simple replacement of letters (in two)
The encipher of a simple replacing can not be called very certain. It is non at all difficult to crack if you compare several encrypted sentences OR know the principles of use. But you can experiment and diversify the method acting. E.g., determined your own decree for replacement letters, add numbers, etc.

One of the encryption options delineate in Conan Doyle's short tarradiddle "Dancing Men"
Mnemonic code
You can economic consumption the favorite method of magicians and magicians - mnemonics. Information technology helps to visualize an object with its full verbal description, thereby simplifying memorization or recognition. A similar principle is used in the well-known saying about the colours of the rainbow: "Each (Red) Hunter (Orange River) wants (Yellow) to know (Common), where (Blue) sits (Dreary) pheasant (Purple)."
In a simplified form, IT looks something like this: "a is ananas, b is banana, c is cherry." To build a password, use the words corresponding to the letters.

Memory the sequence of colors of the rainbow
For example, you need to create a password for bank.com. Let's rent as a basis the code from the first cardinal letters of the nominate of the web resource "b" and "a". According to the design of "b is for banana tree, a is for apple" we make "bananaapple". Tot a hyphen 'tween them and the password will also acquire the necessary type. And if you combine totally this with a acicular surrogate cipher, the password for camber.com will become truly trustworthy nsmsms = s [[; r .
Site name at the finish of the password
Luis Corrons, Technical Director for Network Security at Cat bear Security, offers the undermentioned option:
To make the parole unique for for each one site (without having to drop a line it down), you can impart the appoint of the net resource to its end.
Let's take a closer look at the example of the same cant.com website. Tot up the prefix "-bank" to the selected password at the end. This will result in a more complex design that makes the password some clear and complex. We do the same with accounts connected the social networks "-chitter", "-facebook" and "-linkedin" or shortened options like "-twit", "-face" and "-linkup".
Time frame
There are companies that force their customers to switch passwords all half dozen months or a year. Here you buns also find a solution. Just add the required year, quarter to the beginning or end of the watchword. Aim the close banana password atomic number 3 a ground, tally the future 2016 and the 1st draw and quarter to it. IT turns out banana tree-16-q1 . And if you move only combined key on the keyboard, the password will become significantly to a greater extent complicated and will take the form nsmsms = 3-25 = j3 .

And here is our unique password, rather daedal, honest, which rump be remembered and regularly changed without much difficulty (for months or years).
Size matters
In addition to encryption, it's worth talking about the quality of the password itself. Its duration is valuable. The full set includes 26 lowercase letters, 26 capital and 10 digits. Also, approximately 30 special characters can be used in the password. This all suggests that for each character added to the password, the number of possible options increases by 90 times.
Accordant to Vincent Burke, CEO of FlowTraq Network Protection,
Nearly websites and companies need passwords that include a combination of at least 10 lower and upper character characters, including a number and unitary surgery more special characters

Recently, security experts let recommended increasing the password length to twelve characters altogether. In their opinion, 12 is a borderline. This theory was vermiform on the basis of a study that was conducted at the Institute of Technology (Georgia, USA). Researchers old groups of video card game to crack eighter from Decatur-finger's breadth passwords and came to the closing that two to three hours are enough for this. For hacking, lifelike processors were used - system components designed to take on the needs of new gamers.
Sevener-character passwords qualify arsenic "hopelessly inappropriate". Researchers involved in information security own concluded that hacking twelve-character passwords with modern engineering will take about 17,000 years. Genuine, field developing is so rapid that it is difficult to give accurate forecasts.
Password Originality
Of course, not only length makes the password strong. IT should non be easy to guesswork or predictable. For instance, LadyGaga word is skillful only for a loyal fan or for the singer herself. The set of numbers pool 1234567890 will non put to work either - it is too evident that even a child can crack it by typing all ten numbers in a row on the keyboard. The combination from the password1234 series will also be undependable, even if it consists of dozen characters.

It is worth coming up with tangled and non common passwords. Information technology is meliorate to obviate words that can be found in dictionaries of any lyric. Popular substitutions of letters with numbers (0 instead of "o", 4 rather of "a") do not play a special role. IT is not advisable to ingeminate the same password many times. Although this is exactly what users execute, accordant to a November RSA study, 69%. The results showed that consumers repeatedly employ the password they once unreal (contempt the fact that almost 50% of them were victims of attacks away hackers).
Suggestions
Most security experts agree that passwords should be well-off to remember, simply hard to guess. Likewise complex and insoluble combinations of characters wish bu be forgotten. And writing down passwords on stickers, pieces of paper, in notebooks operating room someplace else is not a good approximation. Here it is better to terminal point itself to a hint that is understandable only to the owner, but not to someone else.

One of the options that makes a countersign more than complicated is to use really hard structures. Information technology is unlikely that anyone leave live able to remember a set of twenty characters, like GdzIQaZyVaFgbh7dlu46. As a matter of fact, such passwords are quite "painful" to use at all. Connected the other hired man, IT will actually be fractious to crack. Such passwords are well for systems that require special security and are not used often.
Arsenic a password, you can use the idiomatic expression, pre-encoding it. For example, in English, "I want to be at the beach" in encoding may look like iw2b @ theBeach . A memorable password that will comprise difficult enough to crack. For each arrangement, it is possible to choose a different closing. Some systems even allow you to use complete sentences American Samoa passwords. Such passwords wish not be disregarded and bequeath be quite trustworthy.
To increase data security, Dropbox has created a list of passwords that are forbidden to use. The list contains about 85100 passwords.
And the University of Southwestward Wales conducted research, the results of which showed that:
4.7% of users habit the watchword password;
8.5% of users choose one of two options: watchword or 123456;
9.8% of users pick out unmatched of troika options: password, 123456 or 12345678;
14% of users choose indefinite of the 10 most popular passwords;
40% of users choose one of the 100 most popular passwords;
79% of users choose one of the 500 most popular passwords;
91% of users select one of the 1,000 all but popular passwords.

And here are the top 25 most popular passwords in the world:
password
123456
12345
12345678
qwerty
123456789
1234
baseball game
Dragon
football
pussy
1234567
monkey
letmein
abc123
111111
mustang
admittance
shadow
master
michael
superman
696969
123123
batman
DOWNLOAD HERE
GET How to make a password secure and memorable / ua-hosting.company Blog / Sudo Null IT News FREE
Posted by: brownagen1949.blogspot.com
0 Response to "GET How to make a password secure and memorable / ua-hosting.company Blog / Sudo Null IT News FREE"
Post a Comment