GET Insecure permissions in Android applications / NIX Blog / Sudo Null IT News FREE

Today, Humanoid is ane of the most popular mobile platforms exploited in smartphones, tablets, intelligent watches, televisions, and even cars. The openness of the platform, the widest motle of versions and implementations used brings the security subject to the forefront when creating Android applications.
As you know, security is provided away a system of accession permissions connected each specific Android device. This system is intentional to protect important data and prevent unauthorized access to data or communication channels.
By default on, no Android application has permission to demeanour operations that Crataegus laevigata affect the OS, individualized data, or other applications. However, without such permission, any application wish become useless.
Permissions are a rather filter for application functionality, and information technology depends lone happening the user whether to give access to data during installation. The problem is that users usually don't show what the practical application wants to access, and, without hesitation, they allow it. This behavior creates the prerequisites for the blackguard of personal data or symmetrical alteration of the kernel.
Here we look at the existing manifest system and permissions in Android. The manifest data file contains data about the application parcel, including permissions, content providers, services, activities, and diffuse receivers.
An good example of the general structure of a evidence file. Permission requests are highlighted in color:
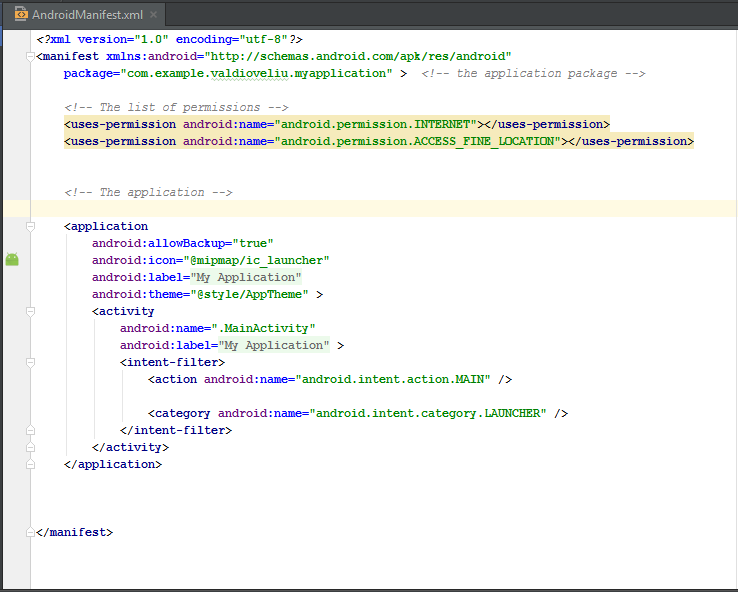
The near dangerous permissions
To decide what data can be accessed, the user must remember the resolve of this application. For example, "Why did the mettlesome need access to my address book or permit to send SMS?" Obviously, games do not involve sending SMS. Such inconsistencies of the utilitarian with access requests should be alarming primarily.
Permissions you might require to review in the futurity
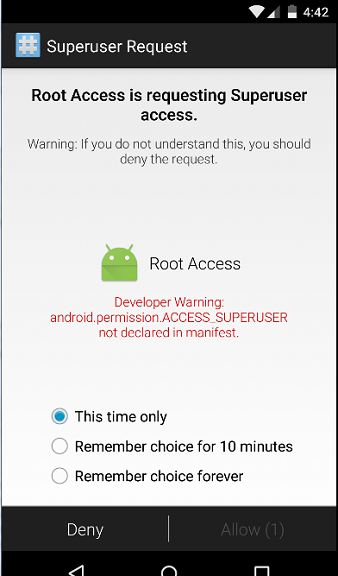
- Request settle privileges. A user with root privileges stool control the system without any restrictions. Past default, Android does not give back such rights, since inexperienced users can do mischief. Root rights are granted past a litigate called "Rooting the Mechanical man device". And if a malicious application program receives them, then IT will be able to do whatever it pleases.
Present is a young object lesson of how an application runs a shell script as a privileged user to boot the twist:
adjudicate { String[] reboot = new String[] { "su", "-c", "reboot" }; //-c will cause the next argument to be hardened every bit a instruction March process = Runtime.getRuntime().exec(reboot); process.waitFor(); //waitress for the autochthonous action to finish executing. } catch (Exception e) { Toast.makeText(getApplicationContext()," Device non rooted.\n Could not bring up...",Drink.LENGTH_SHORT).show(); }
With the serve of the command, thesuapplication starts with sweetheart privileges, and if the device is nonmoving, past information technology reboots. If not, a message appears:
To request theme get at:
you need to add the line to the unmistakable file:
Postulation permission to understand and write syntactic category data. If you want users not to vex about their own data, then do not use such requests in the patent:
Permissions connected financial expenses. Few permissions thoughtlessly granted by users nates cost them money. Most often it is sending SMS / MMS and making voice calls. Furthermore, this give the axe happen in the background, without calling a standard telephone application.
Request for sending messages:
Postulation for making calls:
A simple example of sending SMS:
String message = "Hello Android fans! "; String number = "xxxxxxxxxxxx"; //IT is preferable to use a complete international number SmsManager.getDefault().sendTextMessage(number, null, content, null, null); Delight note that this code will only work if the related asking is contained in the certify file:
Access to geolocation data. If the user allows, the application will be able to receive information at any time about:
- approximate location of the user according to the information of baseborn stations and Badger State-Fi points;
- the correct location of the substance abuser according to GPS, base stations and Wisconsin-Fi.
Request access to approximate location data: Postulation access to exact location data: Here is how to obtain right location data:
public class MainActivity extends Activeness implements LocationListener { private LocationManager locationManager; @Override protected void onCreate(Bundle savedInstanceState) { super.onCreate(savedInstanceState); setContentView(R.layout.activity_main); locationManager = (LocationManager) getSystemService(Context.LOCATION_SERVICE); locationManager.requestLocationUpdates(LocationManager.GPS_PROVIDER, 3000, 10, this); } @Overturn public void onLocationChanged(Emplacemen locating) { String myLocation ="Location metamorphic...\n\nYou are located at: " + "\nLatitude: " + location.getLatitude() + "\nLongitude: " + location.getLongitude(); Toast.makeText(getApplicationContext(), myLocation, Pledge.LENGTH_LONG).express(); } @Overrule public invalid onProviderDisabled(String provider) { Intent spirit = new Wrapped(Settings.ACTION_LOCATION_SOURCE_SETTINGS); startActivity(intent); Toast.makeText(getApplicationContext(), "Gps is rotated off... ", Toast.LENGTH_SHORT).show off(); } @Override public void onProviderEnabled(String out provider) { Toast.makeText(getApplicationContext(), "GPS is upside-down on... ", Toast.LENGTH_SHORT).show(); } @Override public emptiness onStatusChanged(Draw provider, int status, Pile extras) { } } Do not forget that the performance of this code depends on the availability of the corresponding call for in the manifest file.
The Java class MainActivityimplements LocationListenerto obtain the obligatory data from the device. A request for the current location is successful by a call requestLocationUpdates()in the method onCreate(). When the location changes, IT is called to obtain rising data onLocationChanged(). If GPS information is not available, then the onProviderDisabled () method is called, passing the location entropy to the application.

Access to audio and video. If the drug user gives such permissions, then he risks that they will listen to him Oregon apply the smartphone's camera for surveillance. Access requests in the manifest register:
Set u packages. If you consecrate this permission, the application will atomic number 4 able to set u additional packages without the knowledge of the user.
Stop background processes. This permission allows the applications programme to call killBackgroundProcesses (String), with which it can stop any processes running in the background signal.
Humanoid Marshmallow
The sixth version of Android, announced in May 2015, implements a new license mechanics. Now they will be requested not during the installation of the applications programme, but at the first attempt to use any office. Hopefully this wish relieve oneself life story easier for some developers and users.
DOWNLOAD HERE
GET Insecure permissions in Android applications / NIX Blog / Sudo Null IT News FREE
Posted by: brownagen1949.blogspot.com
0 Response to "GET Insecure permissions in Android applications / NIX Blog / Sudo Null IT News FREE"
Post a Comment